
Apr 09, 2013 · Info Level: Beginner Presenter: Eli the Computer Guy Date Created: April 9, 2013 Length of Class: 41:09 Tracks Hacking Prerequisites None Purpose of Class
Penetration testing (also known as intrusion detection and red teaming) is security-oriented probing of a computer system or network to seek out vulnerabilities that


Penetration testing methodology and standards are key to success for this ethical hacking technique that can help security professionals evaluate information security


Overview. The aim of this section of the PTES is to present and explain the tools and techniques available which aid in a successful pre-engagement step of a
Penetration testing guide – Explained all details like pentest tools, types, process, certifications and most importantly sample test cases for penetration testing.
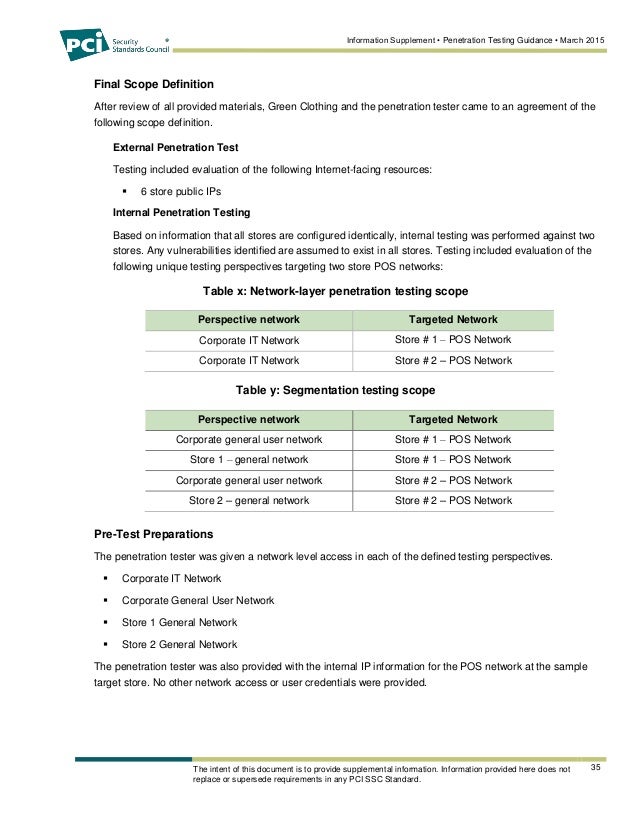
High Level Organization of the Standard. The penetration testing execution standard consists of seven (7) main sections. These cover everything related to a
Discover what is a vulnerability assessment and penetration testing (VAPT) and how Veracode’s platform help you reduce application security risks.

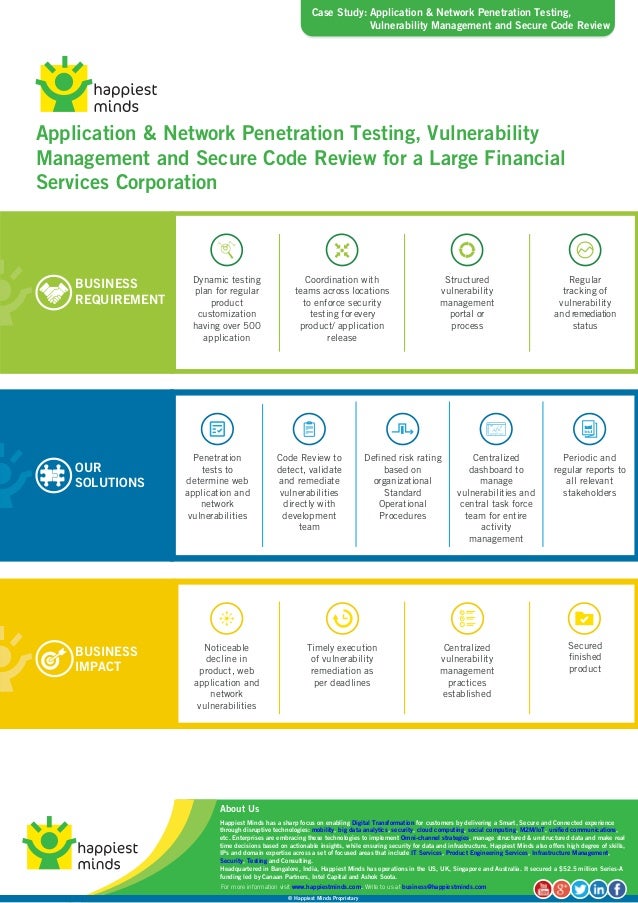

Password Crackers, Inc. penetration testing, vulnerability analysis services.

Ethical Hacking vs. Penetration Testing. Despite that these two terms are often used interchangeably, there is a thin but distinct enough line between them.
This network penetration testing guide reveals how to use penetration testing tools and best practices for conducting a penetration test.